Cyberspace without conflict
The search for de-escalation of the international information conflict
Report
Downloads

Cyber attacks happen on a daily basis, and can have major consequences. Abroad, but also in the Netherlands. For example, foreign hackers attacked hospitals and the harbour of Rotterdam. What can the Netherlands, and other countries, do to prevent escalation? That's what this report is about.
A growing number of countries are capable of carrying out cyber attacks that cause enormous damage to businesses, individuals and government institutions. Almost every country also uses cyber weapons. They spy on one another and try to infiltrate each other’s digital systems; some states even engage in cyber sabotage or spread disinformation. A new type of conflict is being fought with information technology, which we refer to in this report as an ‘information conflict’.
How can the Netherlands contribute to a de-escalation of this information conflict? This report suggests five possible solutions. It calls for the involvement of the public in the political and public debate about international cyber security, since it is the country’s citizens who will be affected most by cyber attacks. At the same time, they are also the ones who can call on governments and politicians to work towards de-escalation.
The nature of cyber attacks
This report first defines what cyber attacks are and compares them with conventional military aggression. The analysis produces the following picture.
Cyber attacks can usually be carried out from a great distance, can spread extremely quickly and are sometimes difficult to detect – especially if they involve highly sophisticated espionage or high-quality falsification of images and sound. Cyber attacks are sometimes even offered as a service. Cyber attackers range from intelligence services to cyber criminals, and seldom have to fear any repercussions, such as facing trial.
At the same time, cyber attacks are not necessarily more harmful than conventional attacks. In fact, cyber attacks are seldom intended to cause serious physical damage and can frequently be neutralised. Once it has been identified, malware can automatically be detected and attacks can be repulsed, provided suppliers and users keep their software systems up to date.
Consequently, while the emergence of cyber attacks creates serious security risks, there are ways of mitigating the damage.
Three rungs on an escalation ladder
Cyber attacks are an everyday occurrence. This report provides an overview of who carries them out, with the emphasis on the role of the major cyber powers – the United States, Russia and China – but also considering the role of the Netherlands and a number of other European countries. It does so by positioning the activities on a so-called cyber escalation ladder. The ladder has three rungs:
- A rung characterised by cyber peace, a situation in which countries do not use digital tools for espionage or engage in sabotage or disseminating disinformation.
- A rung characterised by information conflict, a situation in which states resort to cyber espionage and, sometimes, spreading disinformation and sabotaging digital systems.
- A rung characterised by cyber-physical war, a situation in which the damage caused by states is so serious that one could speak of armed attacks. It should be noted in this context that during a cyber-physical war, every type of cyber attack is in fact covered by international law, not just the few cyber attacks that actually constitute an armed attack.
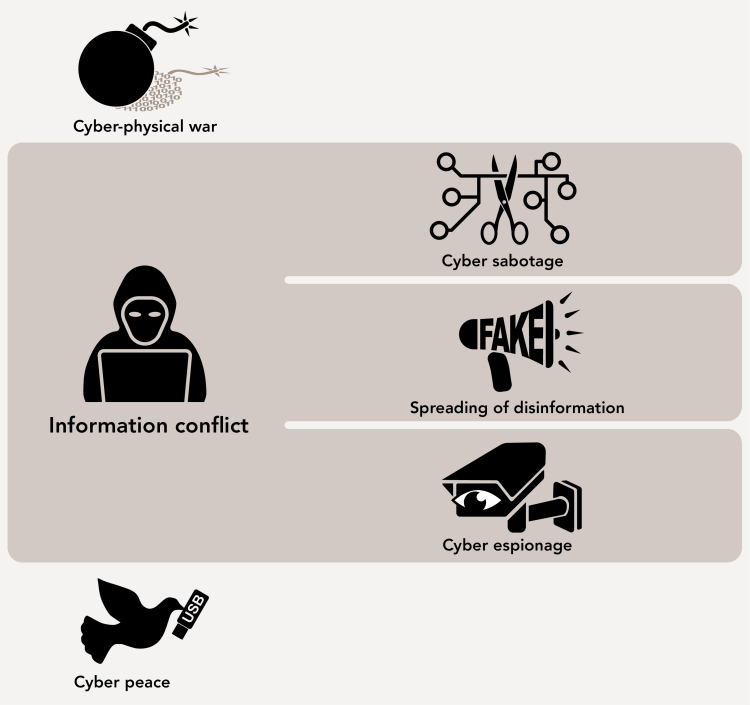
Most actions currently undertaken by influential states fall within the scope of what we describe above as the information conflict. In peacetime, countries build up their cyber security and try to infiltrate the digital systems of other countries as secretely as possible. Russia is also actively spreading disinformation. That is a strategy that other autocratic countries do not yet appear to employ on a large scale, at least not in relation to other countries, but it fits in seamlessly with their desire to control, censor and manipulate the information that reaches their populations. There are also a number of examples of serious cyber sabotage, such as Operation Olympic Games, which has been attributed to Israel and the United States, and the WannaCry attack, which has been attributed to North Korea. Up to now, cyber attacks have never instigated a cyber-physical war; in that respect, there is no ‘cyber war’. However, cyber weapons are increasingly an element of warfare, as can be clearly seen from the conflict in Ukraine.
International cooperation
The continuing information conflict creates a need for international diplomacy and agreements. In this report, we therefore review the cooperation that exists in this field. In various international and regional bodies states are trying to take steps to create a safe and free digital world.
Although there has been some success at the regional level, especially within the EU, states have not yet succeeded in making binding global agreements on cyber attacks. That does not mean there are no rules governing cyber attacks, but because these attacks seldom exceed the threshold of an ‘armed attack’ which activates international humanitarian law, there are only general principles, such as the prohibition of the use of force. And at present those principles are open to various interpretations.
Preferred citation: Hamer, J., R. van Est, L. Royakkers, with the assistance of N. Alberts (2019). Cyberspace without conflict – The search for de-escalation of the international information conflict. The Hague: Rathenau Instituut
Five possible solutions for de-escalation
The information conflict could escalate. As our report shows, the current international situation is risky and worrying. On the basis of our findings, we formulate five possible solutions that could contribute to a de-escalation of this conflict.
1. Continue cooperating to increase international cyber security
Important international initiatives have been taken to improve the security of cyberspace, such as the IMPACT coalition, the European network of Cyber Emergency Incident Response Teams and the NATO cyber exercises. The Netherlands has joined them. These collaborative efforts are and will remain very important.
2. Conclude clear international agreements on de-escalation in relation to cyber sabotage, disinformation, and cyber espionage
Although the Netherlands and other countries have taken important steps to formulate international rules governing cyber attacks, such as the Tallinn Manual and the Paris Call for Trust and Security in Cyberspace, there are very few binding rules that relate specifically to the information conflict. One option might be a cyber convention.
3. Ensure that the cyber arsenal is responsibly managed
It is important to prevent further proliferation of cyber weapons. That calls for international coordination of the build-up of cyber weapons and for effective collaboration with technology companies in removing vulnerabilities in their products. This collaboration also calls for as much transparency as possible, especially among allies.
4. Protect the independence of technology companies
Technology companies perform a crucial role in creating a secure digital environment. They close the holes in their software and can bring robust digital applications onto the market. It is important to help companies to make their operations as secure as possible. Governments are taking a risk if they insist that companies secretly weaken the security of their products. Governments must therefore regulate both the technology and technology companies in a sensible manner.
5. Invest in a debate on international cyber security
The information conflict must be subjected to a democratic debate: it is citizens who are particularly affected by cyber attacks. Citizens thus must be resilient. It is also up to citizens to give direction to the digital future. De-escalation of the information conflict therefore calls for a public and political debate.
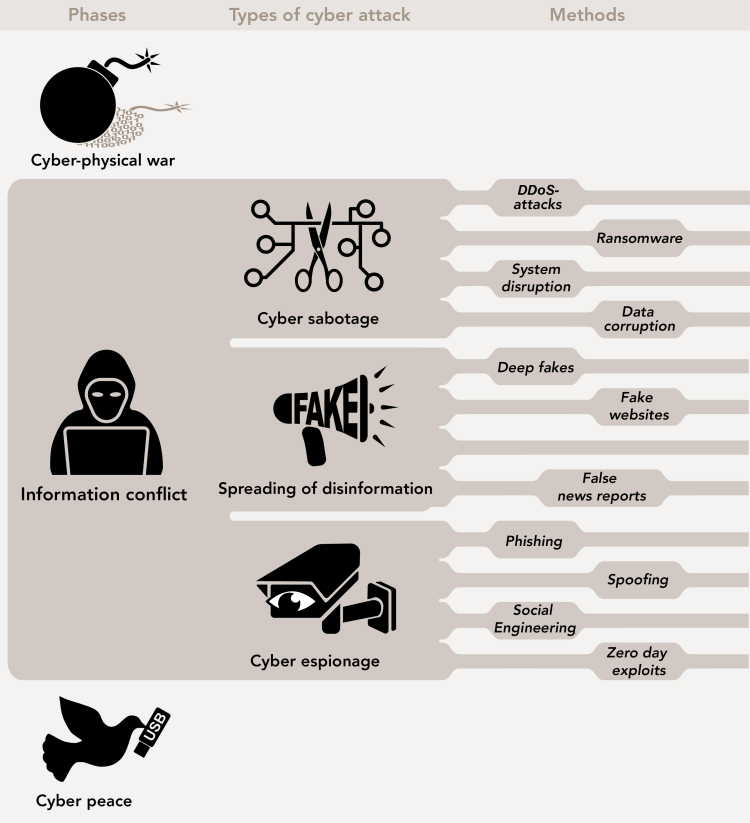
There are 3 types of cyber attack in the phase between war and peace. These are shown in the image below.
Frequently Asked Questions
Our research did not include the chance of a cyber attack on the Netherlands. It is clear though that is is a possibility. The technology to carry out the attacks in the following example already exists.
Imagine that the employees of the Dutch Tax and Customs Administration arrive in the office on Monday morning and find the following message written in bold on their screens:
‘YOUR COMPUTER HAS BEEN HACKED BY THE MOTHERLAND WARRIORS’
Their computers have been hacked and the hackers appear to have gained access to sensitive tax data. And it is not only the Tax Administration that has been hit: the ‘Motherland Warriors’ have also attacked numerous other sectors in society. Banks’ online services have crashed under the strain of heavy cyber attacks. Telecom companies have also been infiltrated. The Dutch oil and gas exploration and production company NAM is unable access its supply data. To cap it all, the online environment of hospitals has been hijacked. The threat is always the same: unless economic sanctions against Russia are lifted immediately, essential information will be deleted from the computer systems and private information will be disclosed. Although nothing can be proved with certainty, there are strong indications that the attacks were launched from Russia.
This is not a fanciful scenario. It is more realistic than ever since the technology exists to carry out all of the attacks in the example. In point of fact, these types of attack have all been carried out at one time or another:
- In 2012, Saudi Aramco, one of the world’s largest oil companies, took all of its services offline for five months after it had been attacked by a group calling itself Cutting Sword of Justice. The attack was attributed to Iran.
- From 2011 until 2013, the Belgian telecom company Belgacom (now called Proximus) was hacked. Hackers reportedly gained access to communication within NATO, the European Council, the European Commission and the European Parliament. The Belgian public prosecutor pointed to the British intelligence service GCHQ as the culprit.
- In 2015, the data of more than 700,000 citizens were stolen when the federal tax administration in the United States, the Internal Revenue Service, was hacked (Crawford 2016). The identity of the perpetrators is not known.
- In the summer of 2017, hospitals throughout Europe, and particularly in the United Kingdom, were infected by the Wannacry malware, which hijacked valuable data.The attack was attributed to North Korea.
- And at the beginning of 2018, the networks of the ING and ABN Amro banks were disrupted by a nasty Distributed Denial of Service (DDoS) attack, which was probably carried out by Jelle S., an 18-year-old youth.
There are three types of cyber attack:
Cyber espionage is the clandestine gathering of intelligence using digital technology.
- Phishing
- Spoofing
- Social Engineering
- Zero day exploits
Cyber sabotage is consciously causing damage to persons, objects or data sets using digital technology.
- DDoS-aanvallen
- Ransomware
- Data corruption
- System disruption
Disinformation refers to the spreading of untrue, inaccurate or misleading information that is consciously created and disseminated for economic gain or to harm a person, social group, organisation or country.
- Deep fakes
- Fake websites
- Fake news
These three instruments can harm a society to varying extents and are therefore described in this report as cyber weapons. They can also be combined to achieve particular strategic effects. At election time, for example, a malicious party can cause the website of a political organisation to crash (cyber sabotage), steal sensitive secrets (cyber espionage) and spread false reports (disinformation). The entire assortment of cyber weapons at an actor’s disposal is referred to as a cyber arsenal.
In this study, we describe the capacity to launch cyber attacks as offensive cyber capability. By this we mean not only access to the technology, but also aspects such as having at one’s disposal expert hackers who can carry out attacks, and having a strategic policy on the use of these capabilities. A cyber operation is a series of actions using digital technology, by an intelligence service for example, such as a cyber espionage operation.
The Rathenau Instituut's task is to support the public debate and political decision making on the subject of the impact of technology on society. This also includes cyber attacks. This report is linked to earlier research, such as our report 'Een nooit gelopen race'. What we hope to achieve is that, besides experts and administrators, citizens also understand what is going on in cyberspace, and join the debate.
The emergence of offensive cyber capabilities has altered the international environment in which the Netherlands finds itself. The central research question in this report is therefore:
How can the Netherlands, in light of the emergence of offensive cyber capabilities, contribute to de-escalation of the information conflict?
To answer that question, in this report we outline the international situation with regard to offensive cyber capacities in three steps.
- First, we explain the nature of offensive cyber capabilities: What are offensive cyber capabilities? We answer that question by reviewing various aspects of cyber operations and what they imply for the relationship between attackers and defenders and compare them with conventional espionage, propaganda and military capabilities.
- We then examine the build-up of capacity by a number of global players: What offensive cyber capabilities are being developed in the United States, Russia, China, the Netherlands and European countries?
- Finally, we examine the ways in which countries collaborate with one another and with partners in civil society at international level in designing measures to regulate offensive cyber capabilities and so could contribute to lasting cyber peace: What joint steps are being taken by the international community to guarantee a safe and free digital world?
We answer the main question on the basis of a description of the international situation.